A New Cybersecurity Reality:
How 70% of Breaches Today Are Executed Without Malware
A New Cybersecurity Reality:
How 70% of Breaches Today Are Executed Without Malware

Introduction
The ever-evolving landscape of cyber threats has taken a surprising turn. Traditionally, malware has been the go-to weapon for cybercriminals seeking to breach corporate defenses. However, recent studies reveal a shocking trend: 70% of breaches today are executed without the use of malware. In this blog post, we will explore this new cybersecurity reality, understand the tactics used by threat actors, and discuss how organizations can fortify their defenses against these non-malware attacks.
The Decline of Traditional Malware
For years, malware has been the cornerstone of cyber attacks. Viruses, worms, trojans, and ransomware have wreaked havoc on businesses, leading to significant financial losses and reputational damage. However, advancements in cybersecurity technologies and improved threat intelligence have made traditional malware attacks more detectable, leading cybercriminals to seek alternative methods.
Non-Malware Attacks: The New Norm
Non-malware attacks, also known as fileless attacks or living-off-the-land attacks, leverage legitimate tools and processes already present within a targeted system. These attacks exploit vulnerabilities in software, applications, or user behaviors, evading traditional malware detection and enabling threat actors to carry out their malicious activities stealthily.
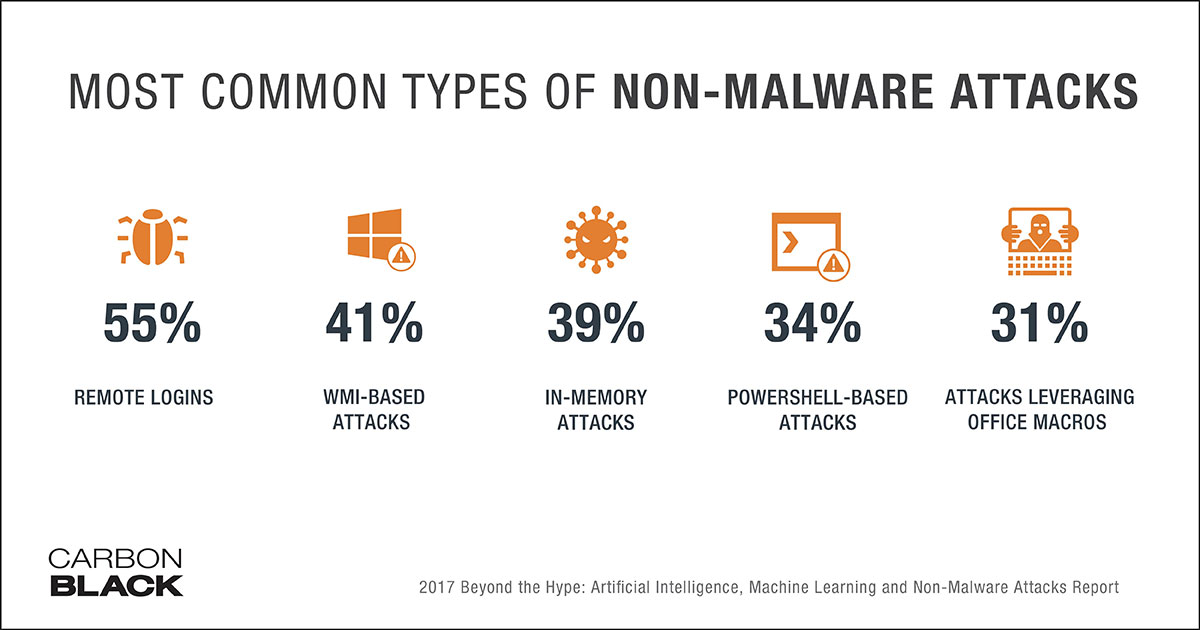
Common Non-Malware Attack Techniques
1. Credential Theft: Cybercriminals use phishing, social engineering, or brute-force attacks to steal user credentials. Once inside the system, they can move laterally and escalate privileges without leaving any malware traces.
2. Remote Desktop Protocol (RDP) Exploitation: Attackers exploit poorly secured RDP connections to gain unauthorized access to a system. Once inside, they manipulate system settings and exfiltrate sensitive data without the need for malware installation.
3. PowerShell Attacks: PowerShell, a legitimate scripting language, is often abused by cybercriminals to execute malicious commands, download payloads, or conduct reconnaissance activities without dropping any malware files.
4. WMI (Windows Management Instrumentation) Abuse: WMI, a powerful administrative tool, can be exploited by attackers to execute code and carry out malicious activities while remaining hidden from security tools.
5. Supply Chain Attacks: Threat actors infiltrate trusted software supply chains and inject malicious code into legitimate software updates, compromising thousands of systems without deploying any malware.

Preventing and Mitigating Non-Malware Attacks
As the threat landscape evolves, organizations must adapt their cybersecurity strategies to defend against non-malware attacks effectively:
1. Employee Training: Educate employees about the dangers of phishing, social engineering, and other social attacks. Encourage a culture of vigilance to reduce the risk of successful credential theft.
2. Access Control: Implement the principle of least privilege to restrict access to critical systems and sensitive data. Regularly review and revoke unnecessary privileges.
3. Network Segmentation: Segment networks to limit lateral movement within the system, reducing the potential damage an attacker can cause.
4. Continuous Monitoring: Employ advanced threat detection and monitoring tools that can identify unusual behavior or patterns indicative of non-malware attacks.
5. Patch Management: Regularly update and patch software and applications to address known vulnerabilities and reduce the risk of exploitation.
Conclusion
The rise of non-malware attacks highlights the adaptability and resourcefulness of cybercriminals. By exploiting legitimate tools and processes, they can breach organizations’ defenses without leaving behind any traditional malware traces. Understanding this new cybersecurity reality is critical for businesses seeking to protect their valuable data, reputation, and customer trust. By adopting a multi-layered approach to security, staying informed about the latest threats, and investing in advanced threat detection technologies, organizations can strengthen their cyber defenses and stay one step ahead of the ever-evolving threat landscape.

