CrowdStrike Falcon
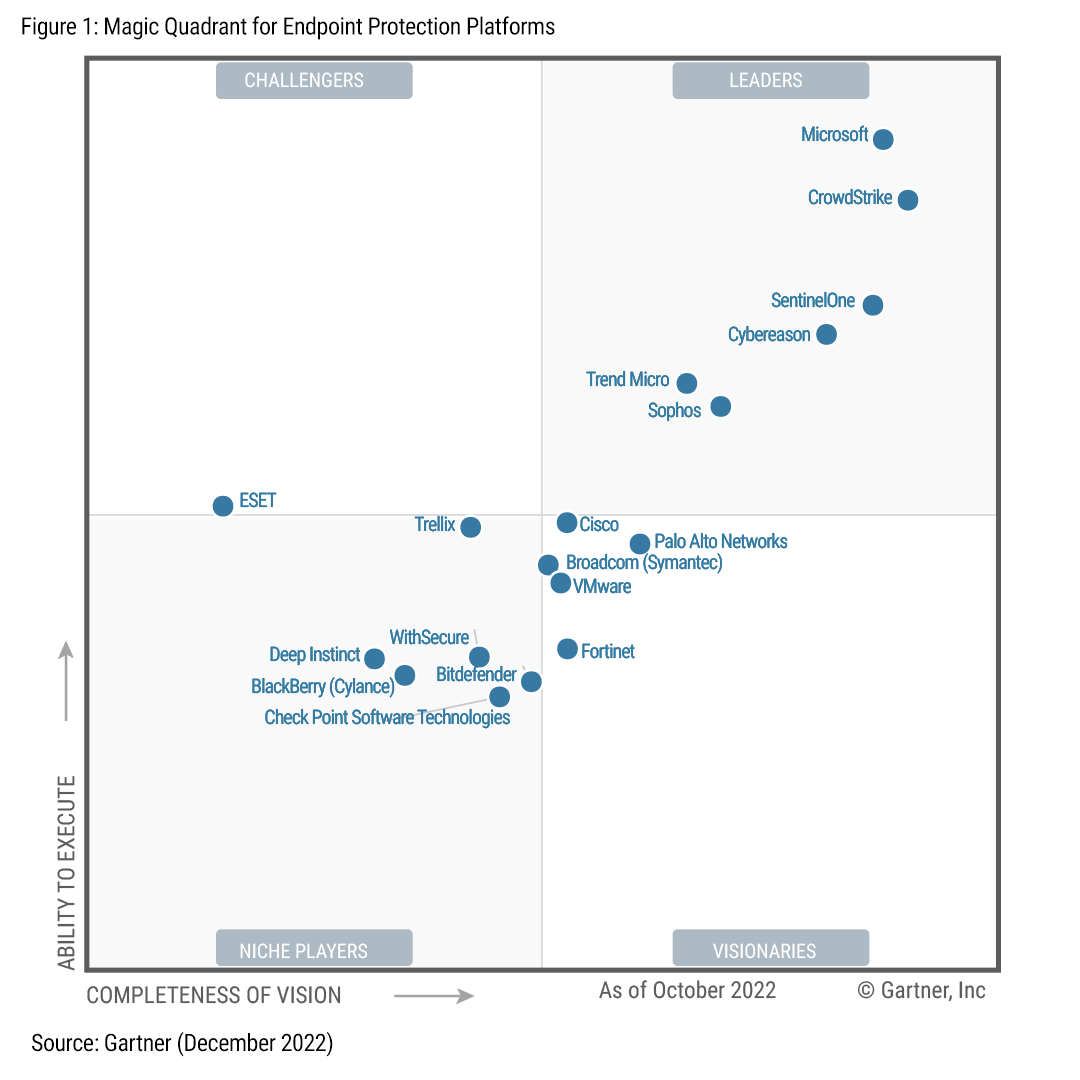
By leveraging our S2 Falcon by Crowdstrike, who is the #1 EDR provider in the world, you get an Endpoint Detection and Response (EDR) platform to enhance your overall cyber security posture and protect your endpoints (devices connected to the network) from sophisticated cyber threats. Our platform provides advanced threat detection, real-time monitoring, and rapid response capabilities, making them a crucial component of modern cyber security strategies. Here’s an overview of the reasons why a company would choose to implement an EDR platform.
Advanced Threat Detection: Traditional anti-virus solutions are often insufficient in detecting and stopping modern, sophisticated threats. EDR platforms use behavioral analysis, machine learning, and threat intelligence to identify malicious activities and suspicious behavior on endpoints, even for previously unknown or zero-day threats.
Real-time Monitoring and Visibility: EDR platforms continuously monitor endpoint activities, collecting vast amounts of data related to processes, network connections, and file executions. This real-time visibility into endpoint behavior allows security teams to promptly detect and respond to potential threats before they can cause significant damage.


Incident Response and Investigation: EDR platforms enable efficient and effective incident response by providing detailed information on the attack vectors, scope, and impact of a security incident. Security teams can investigate incidents thoroughly, trace their origins, and implement appropriate remediation measures.
Endpoint Protection and Isolation: When a threat is detected, EDR platforms can automatically respond by isolating the compromised endpoint from the network, preventing lateral movement of the threat and limiting its impact. This proactive approach helps contain incidents and prevents further damage.
Threat Hunting Capabilities: EDR platforms support proactive threat hunting, allowing security analysts to search for potential threats or indicators of compromise across all endpoints in the organization. This proactive approach helps identify and neutralize threats before they become widespread.
Insider Threat Detection: EDR platforms can detect unusual or suspicious behavior by insiders, such as employees attempting unauthorized access or data exfiltration. This capability is crucial for protecting sensitive data and intellectual property from internal threats.


Compliance and Reporting: Many industry regulations and data protection laws require organizations to maintain strong endpoint security. EDR platforms provide the necessary logs and reports to demonstrate compliance with these regulations.
Automated Response and Remediation: EDR platforms can automate the response to certain types of threats, reducing the burden on security teams and enabling faster containment and remediation.
Threat Intelligence Integration: EDR platforms can be integrated with threat intelligence feeds to stay up-to-date with the latest threat indicators and attack patterns, enabling better defense against emerging threats.
Scalability: EDR platforms are designed to handle large-scale deployments and offer centralized management, making them suitable for organizations of all sizes.
In summary, leveraging our EDR platform is essential for companies looking to strengthen their cyber security defenses, enhance threat detection and response capabilities, and protect their valuable endpoints from an ever-evolving landscape of cyber threats.


